MONITORING DATA CHANGES WITH DATABASE LOG IN DYNAMICS 365 FINANCE AND OPERATIONS
CONTENT Introduction Why database log is critical for sox Key tables and fields for SOX logging Step-by-step: enabling SOX-aligned logging Tips for aligning with SOX controls What database log doesn't do Complementary tools Conclusion |
INTRODUCTION
In SOX-regulated environments, proving that key data is accurate, properly changed, and fully auditable is non-negotiable. Internal and external auditors expect more than high-level assurances—they want verifiable system-generated evidence that data-altering activities are monitored and controlled. This is especially critical for master data and configuration records that directly influence financial reporting.
Microsoft Dynamics 365 Finance & Operations (D365FO) provides a built-in tool—the Database Log—that supports these objectives. When used strategically, it becomes a reliable method to capture evidence for IT General Controls (ITGCs) and automated key controls, allowing organizations to meet SOX compliance requirements directly from within the application.
This article outlines how to configure and use the Database Log in a SOX-compliant manner, what fields and tables are typically in scope, and how to review the logs during audit cycles.
WHY DATABASE LOG IS CRITICAL FOR SOX
The Database Log supports the first and second lines of defense in a SOX environment:
The table below explains how Database Log features map to specific SOX control expectations.
On the left, you can find the control capability the Database Log provides; on the right, you can find how this helps your organization meet SOX compliance requirements.
|
Control Capability (What Database
Log Enables) |
SOX Compliance Justification (Why It
Matters) |
|
Tracks changes to master and
configuration data |
Supports ITGC – Program Change
Management by ensuring that changes to critical configuration are logged
and reviewable |
|
Captures timestamp, user ID, old/new
values |
Satisfies Control Evidence
Requirements under SOX Section 404 – logs prove that data changes were
authorized and monitored |
|
Provides system-generated, immutable
logs |
Enables auditability of key
system controls, which auditors require for walkthroughs and control
testing |
|
Detects unauthorized or unapproved
updates |
Helps mitigate financial
misstatement risks by identifying configuration tampering or fraud |
|
Complements workflow approvals with
field-level logging |
Supports control operating
effectiveness by ensuring the final values match what was approved, not
just that a workflow was completed |
Auditors routinely ask for evidence that configuration values (e.g., posting profiles, bank accounts, tax parameters) have not changed unexpectedly. The Database Log gives you a timestamped, user-specific record of those changes—including the before/after values.
Without it, organizations often scramble to piece together email threads or screenshots—none of which meet the bar for system-generated audit evidence.
KEY TABLES AND FIELDS FOR SOX LOGGING
This section advises which specific tables and fields in D365FO should be monitored via Database Log in a SOX-compliant environment. It directly answers the question:
"What parts of the system should I enable Database Log on to satisfy SOX auditors?"
You're essentially curating a SOX logging scope—focused only on the configuration and master data elements that impact financial reporting and compliance.
Here are common objects that should be considered for Database Log configuration in a SOX-compliant implementation:
|
Table |
Fields to Log |
Why It Matters |
|
VendBankAccount |
Bank account number, Routing number |
Fraud prevention & payment
redirection risk |
|
LedgerPostingSetup |
Posting profiles, Main accounts |
Impact on financial statements |
|
MainAccount |
Posting type, Account category |
GL reporting structure |
|
Ledger |
Fiscal calendar, Reporting currency |
Disclosure and period-end reporting |
|
InventModelGroup |
Inventory valuation method |
COGS calculation |
You're not logging everything—only SOX-sensitive fields that can impact the financials or introduce fraud risk.
This sample list helps define your logging scope, often maintained as part of your SOX control matrix.
Every field listed should map to a SOX control objective (e.g., “Changes to posting configuration must be logged and reviewed”).
STEP-BY-STEP: ENABLING SOX-ALIGNED LOGGING
In this guide, we will enable change tracking functionality for vendor bank accounts.
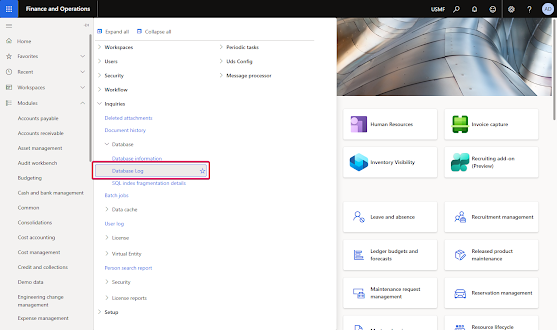
Navigate to database log setup. System administration > Setup > Database log > Database log setup.
Click + New.
Click Next.
Select tables and fields.
Vendor bank account table is under General Ledger.
Expand the note and select the fields that need to be tracked.
Limit field selection to SOX-relevant configuration items only. Avoid enabling it for operational or high-volume transactional tables.
According to our scenario, we will track the following fields.
- Account num
- BankIBAN
- Modified by
- Modified date and time
- Vendor account
Choose the logged events. Enable Insert, Update, and/or Delete based on your SOX control narrative.
Click Next.
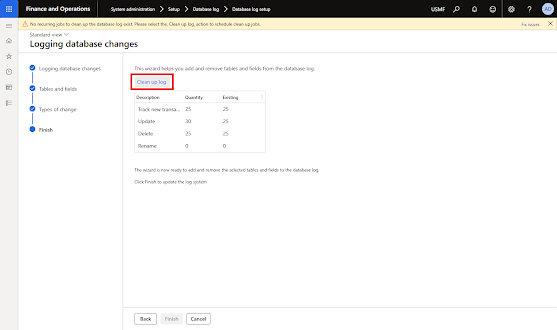
System doesn't allow you to continue before deleting existing database log.
Note that Finish button is now enabled.
Click Finish to complete the wizard and enable logging.
Note that you now see all tracked fields on the database log setup screen.Making changes on the vendor's bank account screen.
Navigate to Accounts payable > Vendors > All vendors.
Select a vendor and click Bank accounts.
Vendor bank account form is now opened.Click Edit button.
Add '9' at the end of the bank account number field value.
Save the screen, close the form.EVIDENCE GENERATION FOR SOX AUDITS
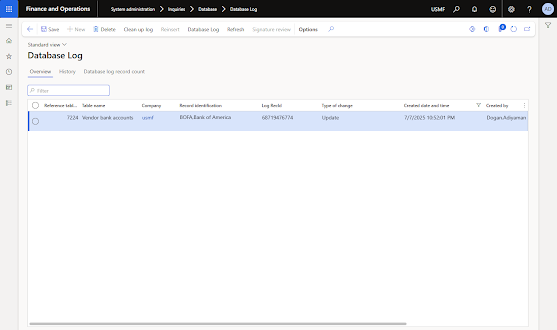
Once enabled, logs become available under:
System administration > Inquiries > Database > Database log.
You can export logs to Excel, filter by user/date/table, and review changes in detail.
|
Logged Attribute |
SOX Value |
|
Timestamp |
Validates when a change occurred |
|
Changed by |
Identifies the responsible user |
|
Old value |
Ensures no unauthorized
configuration overwrite |
|
New value |
Shows what the system is using now |
TIPS FOR ALIGNING WITH SOX CONTROLS
- Separate duties: Only IT control owners or system admins should configure or disable logging.
- Control design mapping: Tie each logged field to a documented SOX control ID.
- Alerting: Consider combining Database Log with Alerts to notify compliance teams of sensitive updates.
- Change control alignment: Ensure all changes logged were also approved via Change Request or IT ticket.
WHAT DATABASE LOG DOESN'T DO
Database Log is not a silver bullet. It doesn’t:
- Track who approved a change (use workflows for that)
- Cover external systems (e.g., CRM, payroll)
- Replace robust SOD enforcement or Fastpath analysis
It does not log changes made via SQL, which is why production databases should restrict direct write access under SOX principles.
COMPLEMENTARY TOOLS
|
Purpose |
Tool |
|
Cross-app user access review |
Fastpath Assure |
|
Data loss prevention and export
alerts |
Microsoft Purview |
|
Workflow approvals |
D365FO native workflows |
|
Full audit across Power Platform |
Microsoft Dataverse Audit Log |
Use Database Log for configuration integrity, and combine it with these tools for a full compliance coverage model.
CONCLUSION
Database Log is a first-party feature designed for compliance. When configured properly, it satisfies critical SOX control objectives such as:
- Evidence of configuration control
- Traceability of key data changes
- Accountability of users with elevated privileges
For internal auditors, external auditors, and control owners, the value lies in having a system-generated, non-editable, filterable trail—available directly in the ERP system, with no external tools or integrations required.
This makes the Database Log an essential tool in your D365FO SOX compliance toolbox—especially for automated ITGC evidence.